Building Your 90-Day Microsoft Purview Rollout — Part 2: Why Oversharing Is Your Biggest Copilot Risk (and How to Fix It)
When preparing for your Microsoft Copilot deployment, organizations usually focus on licensing, training, and encouraging adoption. However, a key security concern that is often overlooked is the risk of oversharing.
If you're familiar with the term “oversharing,” you might already know what it means. For those who don't, we can help clarify. Oversharing in Microsoft 365 involves granting others access to content and information beyond what is necessary. The importance of oversharing has grown with the rise of tools like Copilot and other generative AI applications.
Copilot's ability to access and summarize information across your entire Microsoft 365 environment, including Outlook, Teams, SharePoint, OneDrive, and more, can significantly boost productivity. However, this functionality also brings privacy and security risks. Any file with open access, whether shared intentionally or exposed accidentally, could appear in unintended contexts and be viewed by individuals who are not supposed to see it.
Oversharing isn’t just a compliance risk; it can damage trust with clients, staff, and stakeholders, making it a major challenge in the 'Copilot-era.' In Part 2 of our Purview Rollout Plan series, we're exploring oversharing: how it happens, why it matters for successful Copilot adoption, and the steps you can take to stop it before it begins. And, spoiler alert: it all starts with visibility.
Missed Part 1? Check out The 90-Day Purview Rollout Plan: From Inventory to Impact for a step-by-step guide to establishing your foundation before addressing oversharing.

How Oversharing in M365 Happens
Oversharing in Microsoft 365 typically results from fast-moving, decentralized teamwork. In this setting, documents are shared rapidly, workspaces are created spontaneously, and governance often struggles to keep up. Here's how oversharing happens:
- Abandoned workspaces with permissions that are still active.
- Open "Anyone" links that remain accessible long after they are no longer needed.
- Missing sensitivity labels, which make it challenging to enforce access control.
- Guest users who retain unlimited access to internal content.
- Default tenant settings that promote openness rather than restrictions, such as permissive sharing defaults and the absence of expiration policies for links, often go unnoticed until they lead to significant exposure risks.
This can lead to a landscape of data over-permissioning, where employees have access to far more information than they really need. In daily operations, this might go unnoticed until Copilot steps in.
Unlike traditional search tools, Copilot not only locates documents but also retrieves, analyzes, and compiles content from across your Microsoft 365 environment. If a file is accessible to a user—even by accident—Copilot can bring it up in a chat, summary, or document. Suddenly, forgotten files in obscure SharePoint folders or Teams chats can reappear in someone’s workflow.
Moreover, because Microsoft 365 lacks a straightforward, centralized way to monitor access, IT and compliance teams often remain unaware of potential data vulnerabilities. If your Microsoft 365 environment contains outdated, misclassified, or excessively shared files, Copilot could inadvertently create a route for data leaks. Existing oversharing problems will only get worse once Copilot starts using this data.
So now, the threat doesn’t come from malicious actors but from well-meaning employees who accidentally share sensitive information. A document sent to a single colleague can easily be forwarded, reshared, and accessed by dozens or even hundreds of people. This could include anything from client contracts and employee performance reviews to financial forecasts and product roadmaps, as well as legal discovery documents and internal strategy decks.
Even seemingly harmless items, such as meeting recordings, project notes, or draft press releases, can contain confidential discussions or unreleased information. Without proper sensitivity labels and access controls, these materials can be surfaced by Copilot or shared externally, creating serious compliance and reputational risks.
Oversharing Detection and Prevention Starts with Visibility
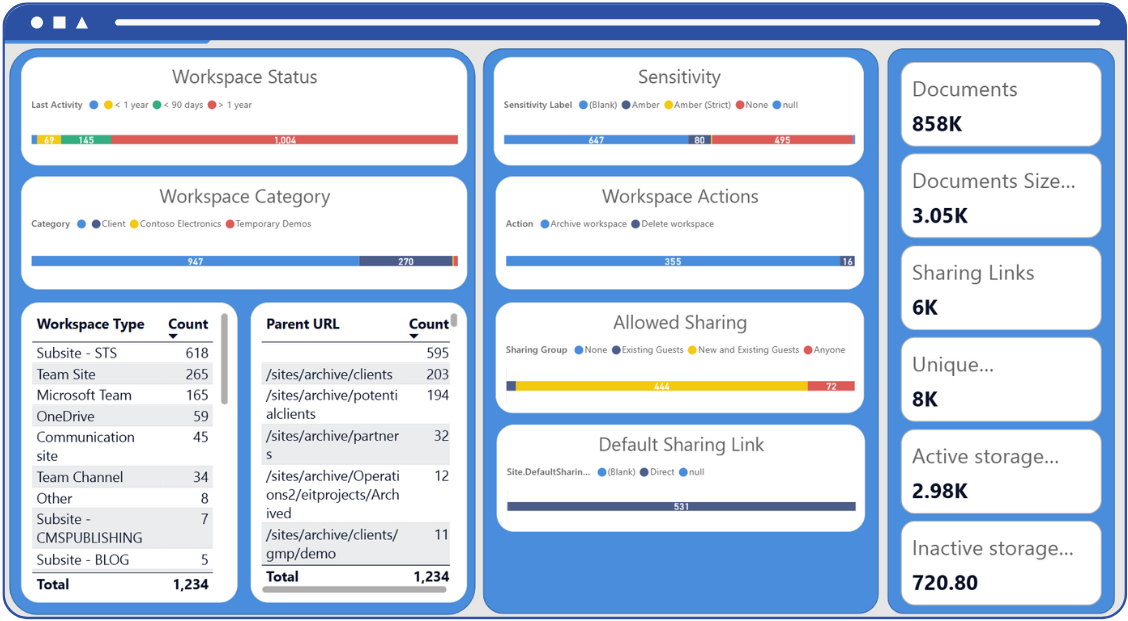
The first step in managing oversharing is to achieve clarity. Visibility is crucial for effective governance; without it, remediation efforts can become guesswork. Envision IT’s Tenant Dashboard, a Power BI-driven tool for tenant cleanup, management, and governance, provides a comprehensive view for monitoring your Microsoft 365 environment's health. It connects with SharePoint, Teams, OneDrive, and Azure AD to deliver actionable insights on:
- Files with overly permissive sharing settings, including anonymous and guest links.
- Workspaces containing inactive or orphaned content may negatively impact Copilot results.
- Sensitivity label coverage, indicating which files are protected and which are not.
- Storage usage and clutter, helping to identify ROT (Redundant, Obsolete, Trivial) data.
The Tenant Dashboard helps administrators find specific files and workspaces that need attention, such as abandoned folders, unused Teams, and documents without sensitivity labels, making the cleanup process faster and easier before Copilot goes live.
This is especially beneficial for regulated industries, where compliance breaches can result in hefty fines or reputational damage. The Tenant Dashboard helps organizations proactively close security gaps, reclaim storage space, and improve compliance, while accelerating Copilot adoption.

Practical Steps for Addressing Oversharing
Oversharing is not just a technical issue; it’s a governance challenge. Addressing it requires a combination of visibility, policy enforcement, and user education. Envision IT recommends the following practical steps to organize your Microsoft 365 environment and prepare for the safe adoption of Copilot.
Audit Sharing Links and External Access
Start by identifying files shared through “Anyone” links or with guest users. The Tenant Dashboard makes this easier by highlighting overly permissive sharing settings across SharePoint, OneDrive, and Teams. Revoke unnecessary links, tighten external sharing policies, and set expiration rules for guest access.
Apply and Monitor Sensitivity Labels
Utilize Microsoft Purview to assign sensitivity labels to documents. Envision IT often supports clients in creating straightforward labelling systems, like a "Traffic Light" method (Red, Yellow, Green), which makes classification easier for users. The Tenant Dashboard tracks label coverage and identifies gaps, helping you maintain consistent protection across your organization.
Clean Up ROT Data
Redundant, obsolete, and trivial (ROT) data can clutter your environment and reduce the usefulness of Copilot results. Use the dashboard's activity tracking feature to identify inactive files and workspaces. Archive or delete items that are no longer necessary to cut storage costs and improve search results.
Review Workspace Permissions
Many organizations encounter issues with "workspace" or "content sprawl," which happens when Teams and SharePoint sites are created without adequate oversight. Envision IT helps clients audit these environments by identifying sites with excessive access permissions or outdated content. Tools like Microsoft Purview, AvePoint Cloud Governance, and the Tenant Dashboard make it easier to set policies, manage site lifecycles, and keep workspaces secure and compliant.
Encourage Responsible Sharing Practices
Governance involves more than just adopting new tools; it also requires fostering a strong organizational culture. It's essential to train employees to recognize the risks of oversharing and how to use sensitivity labels correctly. The IT department often supports this by providing onboarding workflows, policy guides, and in-tenant prompts that promote best practices.
Develop Governance Policies
Define the criteria for who can create Teams, share content externally, or apply sensitivity labels. Envision IT helps clients configure Microsoft 365 policies and develop scalable governance frameworks. This process involves implementing monitoring and auditing tools to ensure compliance with policies and making necessary adjustments.
Customer Success Story
A mid-sized professional services firm was nearing its Microsoft 365 storage limit and facing a costly upgrade. They struggled to identify which files and data could be safely deleted or archived without disrupting their operations. Using the Tenant Dashboard, they quickly identified inactive workspaces and files that had not been accessed recently. With Envision IT's help, they successfully archived over 300 GB of redundant or obsolete data, avoided the need for a storage tier upgrade, and significantly reduced their risk of oversharing, just in time for their Copilot rollout.
Conclusion: Oversharing Is Not Malicious; It Is Often Unmanaged
Oversharing in Microsoft 365 isn't usually caused by malicious intent; instead, it occurs because well-meaning individuals work in environments without clear boundaries. While Microsoft 365 and Microsoft Copilot make collaboration easy, the lack of visibility and governance can quickly turn this convenience into a risk.
Microsoft 365 Copilot does not introduce new security threats; it simply amplifies existing ones. If your tenant has outdated, misclassified, or overly shared content, Copilot will mirror that disorganization in its responses. Sensitive files might appear in unexpected locations, and users could inadvertently access information they shouldn’t.
We always say the solution isn't to restrict collaboration but to manage it effectively. With the right tools, policies, and training, organizations can empower users while protecting their data and reap the benefits of improved collaboration and productivity. Successful and effective Copilot readiness begins with maintaining tenant cleanliness. Oversharing is a governance concern, and now is the time to address it.
Coming Up Next: Part 3 – The Traffic Light Protocol: Simplifying Sensitivity Labels for Users
Data classification doesn't have to be complicated. In Part 3 of our Purview Rollout Plan series, we'll demonstrate how the Traffic Light Protocol makes sensitivity labelling easy for everyone in your organization. Learn how a simple Red-Yellow-Green system can enhance adoption, improve compliance, and protect your data while fostering and sustaining smooth collaboration.
In the meantime, consider exploring these resources to help you get a better handle on oversharing:
- Watch On-Demand: Copilot and Security Readiness Webinar to learn practical tips and best practices for a smooth, secure rollout.
- Launch a Free Scan of the Tenant Dashboard to see how it can help you clean up, govern, and prepare for a secure Copilot deployment.
.png)
Register for our Upcoming Webinar: Hero Links, External Sharing, and Governance in Microsoft 365 – Fireside Chat with Stephen Rice!
Join us for an insightful session featuring Stephen Rice, Principal Product Manager for OneDrive and SharePoint at Microsoft, and Peter Carson, President and CEO of Envision IT. This engaging deep dive will explore the future of sharing and governance within Microsoft 365.
Discover how Hero Links can simplify collaboration, enhance security, and streamline compliance at scale. You'll leave with practical strategies for securing your environment, managing external sharing, and optimizing governance without compromising productivity.
Don’t miss this opportunity to learn from industry experts and transform the way your organization collaborates!